That contortion is just one of several flaws in a prosecution that has been plagued by embarrassing blunders, including misattributing to a Tornado Cash developer text messages that were actually sent by a reporter.
Then, prosecutors called as a witness a woman who had fallen victim to a $250,000 cryptocurrency scam. Their argument seems to have been that Tornado Cash developers should have helped her in ways that were technologically impossible.
But shortly after this testimony, crypto sleuths discovered that the scam victim’s funds likely never were laundered through Tornado Cash at all.
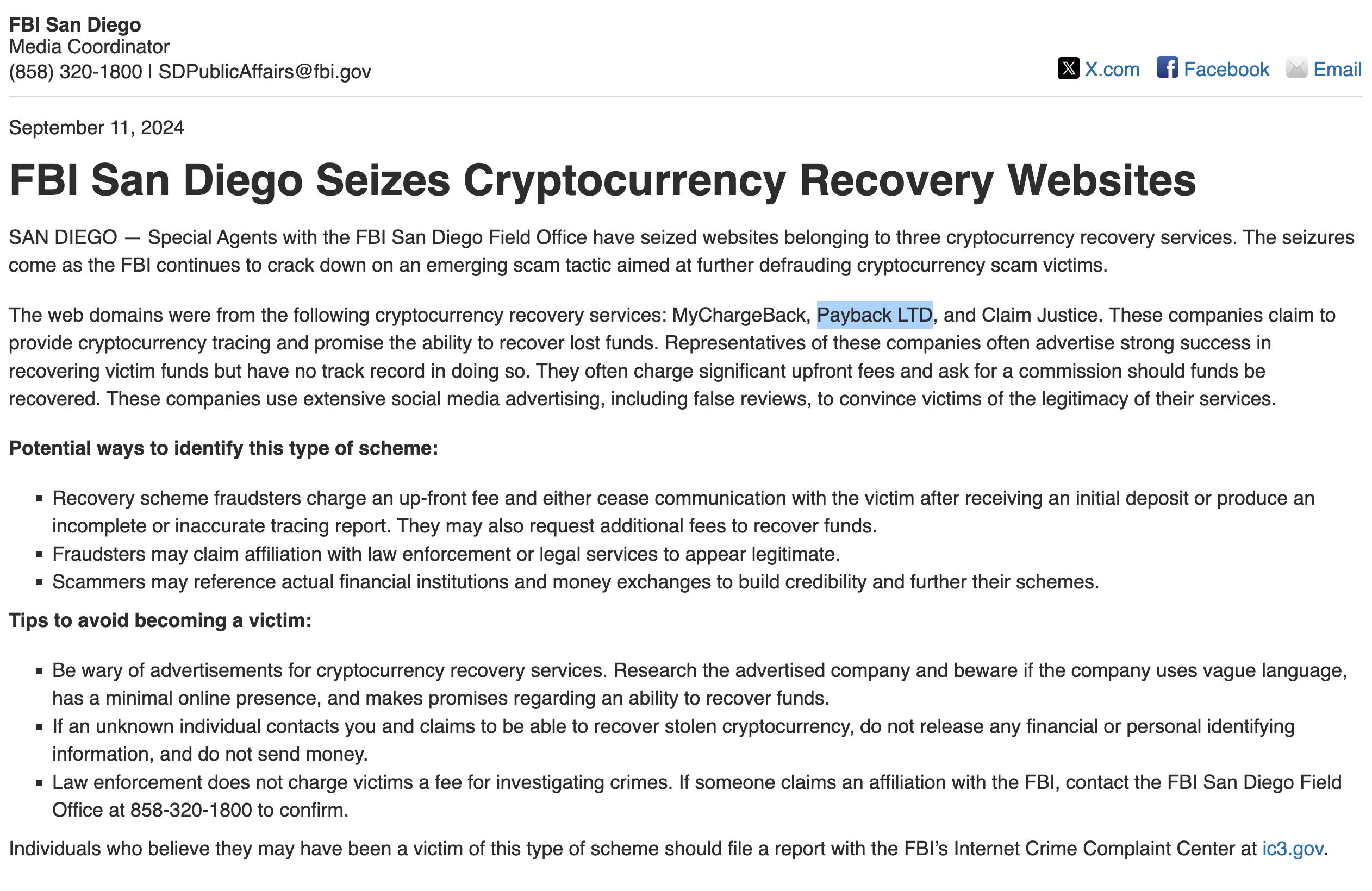
Not only that, the “crypto recovery” service used by the victim may have been one identified by the FBI as a scam known for producing “incomplete or inaccurate tracing report[s]” (though this may be a separate company sharing a name, or impersonating a legitimate business).
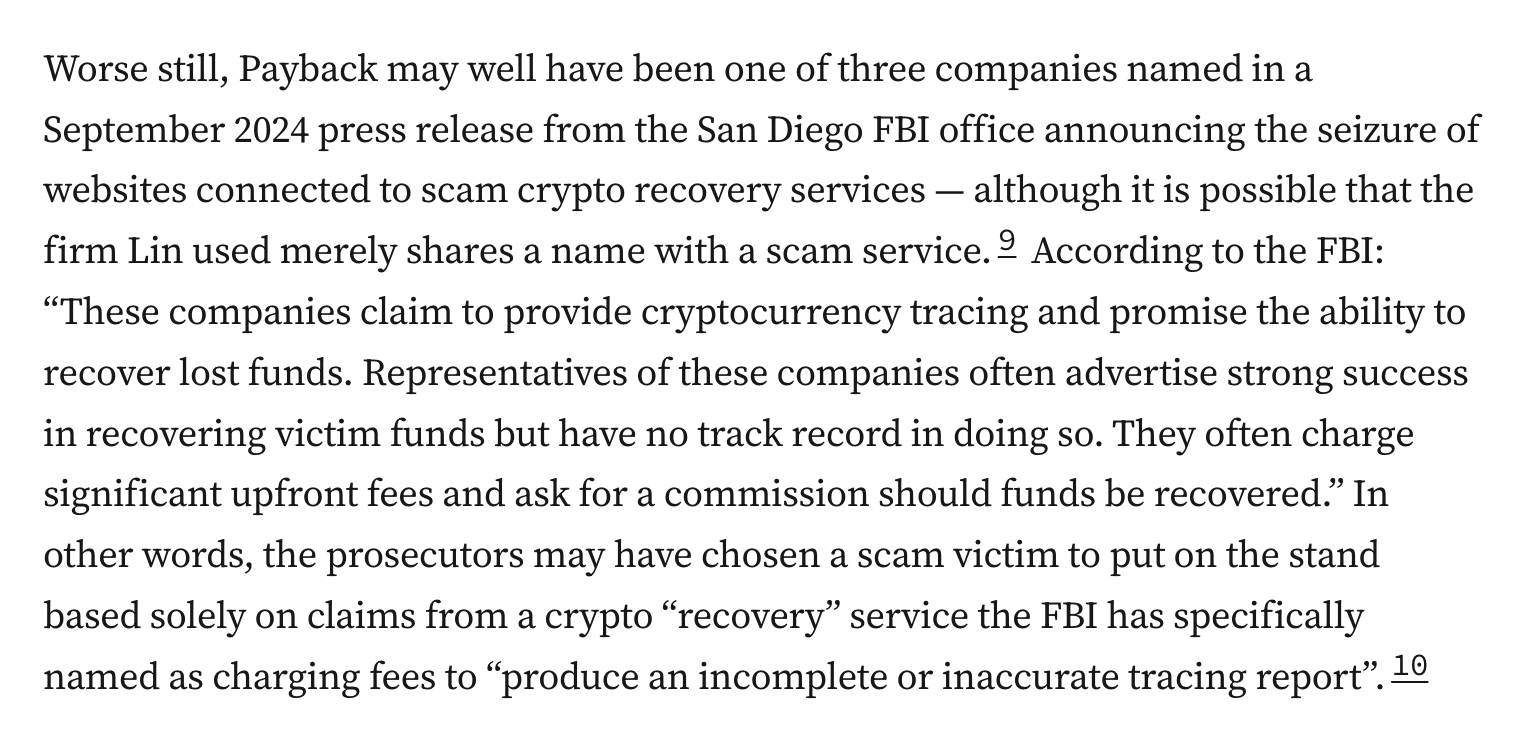

Prosecutors have tried to recover the testimony by bringing in an FBI agent to testify that the scam victim’s funds were sent to Tornado, using an accounting practice known as LIFO. Problem is, that doesn’t really work for crypto tracing — as the agent acknowledged.
![Now, this is admittedly a simplified example. A real money corner store money transfer service is required to register and abide by strict regulations as a money transmitting business, including keeping detailed records on who sent money where. Yet these are exactly the compliance measures that prosecutors, following the Blanche memo, can no longer argue Storm was required to implement.
When asked during cross-examination, “This doesn’t prove that the hacker moved [Lin’s] money into Tornado Cash, does it?” the agent replied “No, not at all.”11](https://media.hachyderm.io/media_attachments/files/114/932/600/412/458/091/original/4dce9167e1703a24.png)
A small Bonfire corner on the internet
This is a small personal instance of Bonfire in the Fediverse.
![The misattributed messages
The prosecution in Storm’s case has really not covered themselves in glory thus far. First, it came to light that they fumbled extracting Telegram messages from a chat including Storm and Pertsev. It turns out a message quoted in Storm’s indictment and attributed to Pertsev, reading “Heya, anyone around to chat about axie? Would like to ask a few general questions about how one goes about cashing out 600 mil”, was actually a message forwarded by Pertsev from a CoinDesk journalist researching a story about the massive March 2022 Axie Infinity theft [W3IGG] and subsequent laundering of stolen funds.4
Although prosecutors have (sort of) admitted they misidentified the message forwarded by Pertsev as one he authored, they’re still arguing that their error is not material to the case, and that somehow forwarding the message made it a statement Pertsev “manifested [and] adopted or believed to be true”. They also claimed the defense waited to raise the issue in a “strategic decision to play ‘gotcha’ on the eve of trial”.5 The defense has petitioned the court to allow them to view grand jury transcripts, citing “grave concerns about the integrity of the grand jury proceedings since it appears that the government provided false information to the grand jury”, and suggested they may move to dismiss the case on that basis.6](https://media.hachyderm.io/media_attachments/files/114/932/583/575/049/996/original/34c0a7beb17fbf8f.png)